What is NAT? Understanding Network Address Translation
What is NAT? Understanding Network Address Translation
What is NAT?
Do you want to know about NAT (Network Address Translation)? NAT is an essential part of the current networking system. The Network Address Translation works as a mediator between connections within a private network & external Internet, which facilitates connection by translating private IP addresses into public ones.
Now, be ready to learn about the functionalities, benefits, challenges, and future prospects of NAT (Network Address Translation). What are you waiting for? Let’s get started!
How Does NAT Work?
| S.No. | Factors | How? |
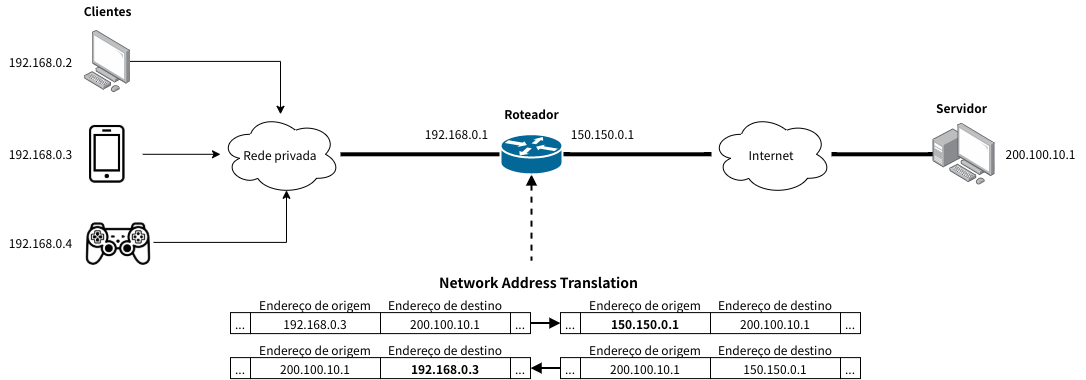
| 1. | Private and Public IP Addresses | NAT enables communication between devices on a private network and internet resources by allowing them to share a single public IP address. Public IP addresses are routable on the internet, but private IP addresses (such as 192.168.x.x, 10.x.x.x, etc.) are only used internally within a network. |
| 2. | Translation Table | A translation database that links private IP addresses and ports to their corresponding public IP addresses and ports is kept up to date by NAT. NAT changes the source IP address and port of a packet sent to the internet by a private network device to a public IP address and a different port number. |
| 3. | Outgoing Packet Modification | Network Address Translation (NAT) converts the source IP address and port of outgoing packets to the public IP address and a distinct port number when a device within the private network tries to communicate with an external server. This makes it possible for several devices connected to the private network to use the same public IP address. |
| 4. | Incoming Packet Translation | NAT uses the translation table to translate the destination IP address and port back to the matching private IP address and port when a response packet from the internet returns to the public IP address and port. |
| 5. | Stateful Connection Tracking | Incoming packets are correctly routed to the correct internal device when NAT maintains stateful connection tracking, which means it records the status of every connection (such as TCP connections). |
| 6. | Types of NAT | There are various NAT varieties, such as:
a) Static NAT: It converts a given private IP address into a given public IP address map. b) Dynamic NAT: It converts private IP addresses from a pool of accessible addresses to public IP addresses. c) Port Address Translation (PAT) or NAT Overload: It uses distinct port numbers to map several private IP addresses to a single public IP address. |
| 7. | Security and Privacy | A certain level of security and privacy is offered by NAT, which shields internal network information from prying eyes. It prevents direct access to internal devices from external networks by serving as a barrier between the internal network and the Internet. |
| 8. | Limitations | Although NAT is useful for improving security and preserving public IP addresses, it can also have drawbacks, such as making it harder to host some services (like peer-to-peer apps) and perhaps creating speed bottlenecks, particularly on large-scale networks. |
Benefits of NAT
1. Security Enhancement
By serving as a barrier between internal and external networks, concealing internal IP addresses from outside sources, and offering some defense against intrusions and attacks, NAT improves security.
2. IP Address Conservation
By enabling several devices on a private network to share a single public IP address, NAT conserves public IP addresses. This lowers the demand for IPv4 numbers and delays the switch to IPv6.
3. Network Scalability
By allowing the creation of private networks without necessitating a corresponding increase in public IP addresses, NAT improves network scalability by promoting effective use of address space and allowing for the growth of network infrastructure.
Challenges of NAT
- Impact on End-to-End Connectivity
By masking internal IP addresses, NAT can interfere with end-to-end connectivity and cause difficulties for protocols or applications that depend on direct host-to-host communication.
- Complications in Peer-to-Peer Applications
Peer-to-peer applications encounter challenges with network area topography (NAT) since they frequently encounter difficulties establishing direct connections between peers behind various NAT devices, necessitating intricate solutions like traversal techniques or relay servers.
- Administration Overhead
In order to maintain appropriate communication between internal and external networks, NAT adds administration overhead to the tasks of maintaining translation tables, resolving connectivity problems, and setting up port forwarding rules.
NAT vs. Proxy Servers
| S.No. | Factors | How? | |
| 1. | Functionality | NAT | Multiple devices within a private network can share a single public IP address for internet access thanks to network address translation (NAT), which essentially converts IP addresses and ports of packets traveling via a router or firewall. |
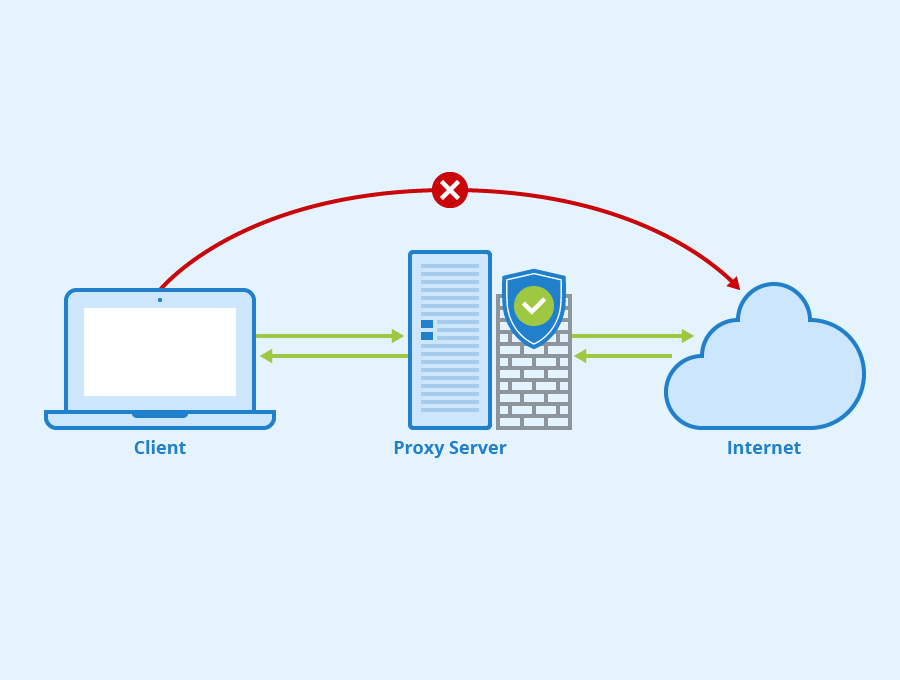
| Proxy Servers | Proxy servers function as a middleman between servers and clients, including web browsers.
Client requests are received, and forwarded to the relevant servers, and then the appropriate servers get the responses, which are then forwarded back to the clients. They can also offer extra security protections and enhance efficiency by caching content. |
||
| 2. | Level of Operation | NAT | It translates IP addresses and ports included in packet headers while operating at the network layer, or Layer 3, of the OSI model. |
| Proxy Servers | Function at the OSI model’s application layer (Layer 7), intercepting and interpreting application-level protocols (such as HTTP and FTP) to respond to client requests. | ||
| 3. | Visibility and Control | NAT | It offers little visibility and control over the traffic that passes through it in most cases. It does not examine the contents of packets; instead, it primarily concentrates on translating addresses and ports. |
| Proxy Servers | Since they can examine and alter both request and response headers, they provide more visibility and control over traffic and enable features like content filtering, caching, logging, and traffic optimization. | ||
| 4. | Usage Scenarios | NAT | Commonly used to improve security and preserve public IP addresses in small to big networks, including as home networks and business settings. |
| Proxy Servers | Frequently used in business settings to enforce security regulations, track and filter internet traffic, speed up web browsing through caching, and give customers anonymity. | ||
| 5. | Impact on Performance and Security | NAT | Usually does not affect performance but conceals internal network information from outside sources to offer a rudimentary security. |
| Proxy Servers | Due to added processing overhead, it may affect performance, particularly when handling high traffic volumes. However, they provide more sophisticated security capabilities like virus scanning, content filtering, and access controls. | ||
Implementing NAT
| S.No. | Installing | How? |
| 1. | Identify Internal and External Interfaces | Ascertain which interfaces are connected to the public network outside and the private network within. |
| 2. | Define NAT Policies | Indicate how internal private IP addresses are mapped to external public IP addresses. |
| 3. | Configure Translation Rules | To specify how IP addresses and port numbers are translated between private and public networks, set up translation rules. |
| 4. | Enable NAT on Interfaces | On the assigned internal and external interfaces, turn on NAT functionality. |
| 5. | Monitor and Troubleshoot | Keep an eye on your NAT sessions and take care of any connectivity problems or slowdowns. |
Future of NAT
NAT’s importance in India is expected to persist because of the country’s limited IPv4 address pool and the country’s ongoing internet user growth. In both home and business settings, network address translation (NAT) will continue to be an essential tool for protecting public IP addresses and boosting network security.
Furthermore, when IPv6 becomes more widely used, NAT might develop to accommodate IPv6 transition mechanisms in addition to conventional IPv4 deployments.
Conclusion
If you want to know more about networking infrastructure and security, you can get in contact with a reliable Institute that can offer you the best learning environment to start your career in networking. For that, you can get in contact with Craw Security which is offering the best-customized course “Basic Networking Course in Delhi” for students who want to pursue a career in the networking domain in the IT Sector.
You will be able to get the best learning environment in the IT Sector with the guidance of professionals on the premises of Craw Security. What are you waiting for? Contact, Now!
Frequently Asked Questions
1. Is NAT the same as a firewall?
No, NAT and a firewall are not the same thing. A firewall monitors and controls traffic according to predefined rules for security reasons, whereas NAT just translates IP addresses and ports.
2. Can NAT affect internet speed?
Indeed, NAT may have an impact on internet speed because of processing overhead and its inability to handle high traffic quantities.
3. Does NAT provide anonymity?
No, NAT does not offer anonymity since it does not mask the source of traffic coming from the NAT device; rather, it merely conceals internal IP addresses from outside networks.
4. What are the security risks associated with NAT?
Certainly, here are five security risks associated with NAT:
- Obscured Internal Hosts,
- Port Forwarding Vulnerabilities,
- Address Spoofing,
- Denial-of-Service (DoS) Amplification, and
- Difficulty in Traceability.
5. Is NAT still relevant in IPv6 networks?
In IPv6 networks, network address translation (NAT) is still applicable for some use cases such as IPv6 transition mechanisms, network address conservation, and security improvements.