What Happens if You Download a Cracked Program?

What Happens if You Download a Cracked Program?
What happens if you download a cracked program?
Spoiler Alert!: Nothing good, to be honest. You will most likely find a backdoor, miner, or stealer in addition to pirated software.
When you need a program but are unable to get an official license just yet, what should you do? The right response is either “Find a free alternative” or “Use the trial version.” “Search online for a cracked version” is the incorrect response.
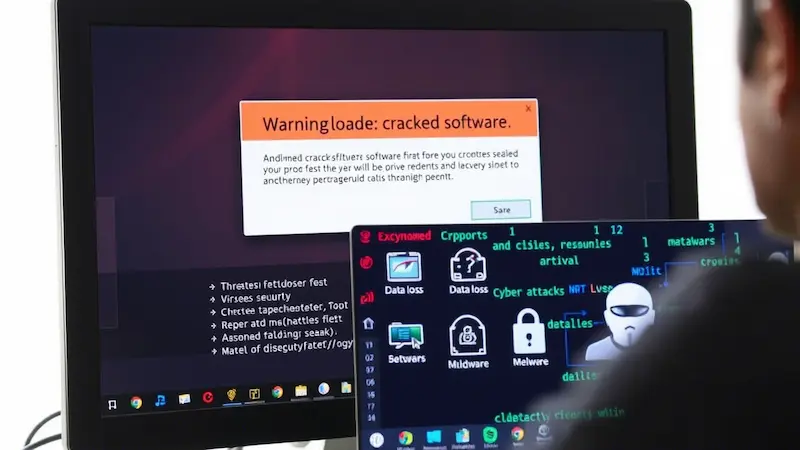
Cracked software and other goodies are often available from dubious alternate sources. You could find the program you want after sifting through ad-filled websites, but it generally comes with a miner, stealer, or other malicious software included for good measure.
We illustrate why you should stay away from websites that provide quick downloads of popular programs using instances from the real world.
Miner and Stealer on Source Forge
SourceForge, the precursor of GitHub, was once the biggest website for all things open source. However, SourceForge still offers software hosting and distribution services, so don’t assume it’s dead. Anyone who wants to can upload several projects to its software portal.
Additionally, this cosmopolitanism is a hindrance to high-level security, just like with GitHub. For instance, our specialists discovered the office package project on SourceForge. It appears innocuous at first: a straightforward name, a simple description, and even a favorable review.
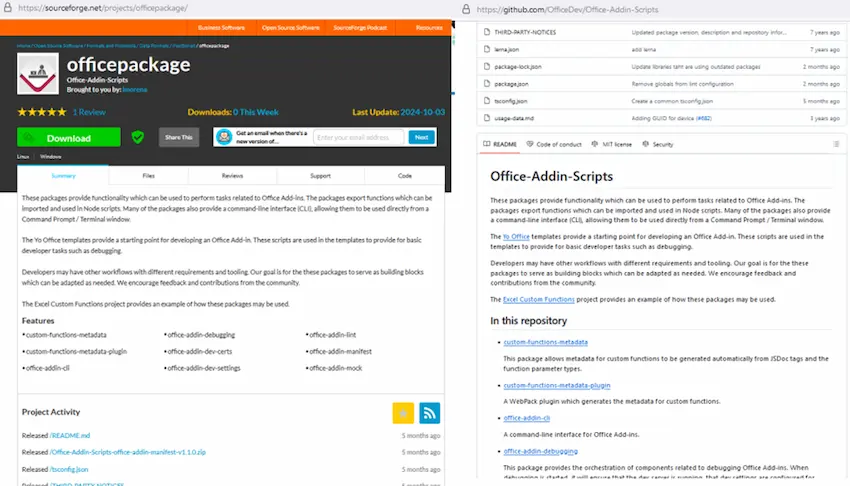
However, what if we informed you that the files and description were directly lifted from a different GitHub project? Already, alarms are going off. However, when you click the Download button, no malware appears on your computer; the project appears to be clean. Evidently, because the malicious payload was sent via the related web page rather than the officepackage project itself. How can this be?
The truth is that each SourceForge project has its own domain name and is hosted on SourceForge.io. Thus, officepackage.sourceforge[.]io is the URL of a project called officepackage. These pages rank well in search results and are readily indexed by search engines. Attackers draw victims in this way.
Users could obtain nearly any version of the Microsoft Office suite by going to officepackage.sourceforge[.]io via a search engine. However, as usual, the details were crucial: a link to https[:]//loading.sourceforge[.]io/download appeared in the browser’s status bar when you hovered over the Download button. Have you spotted the trap? Officepackage is not related to the new link; loading is a completely different endeavor.
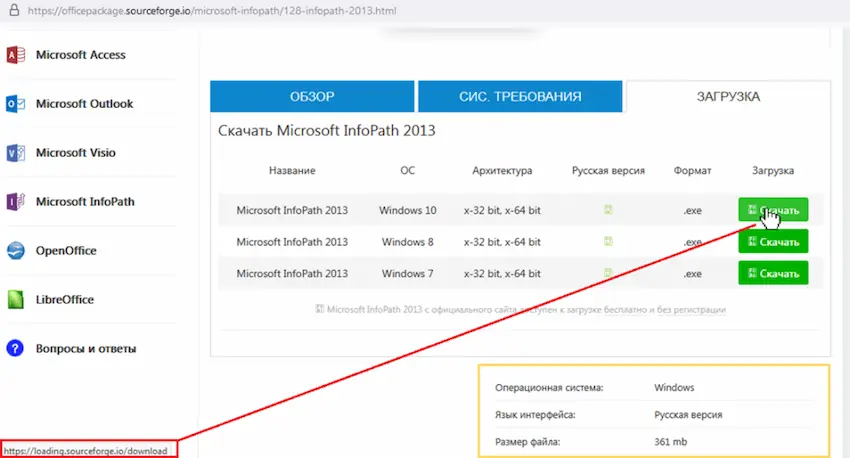
Additionally, customers were taken to another intermediate website with another Download button after clicking, rather than the page of the loading project. The user, tired of browsing, got a file—an archive called vinstaller.zip—only after clicking this. There was a Trojan Windows Installer in the second archive that was contained within.
Two nasty things were at the core of this terrible nesting doll: when the installer was executed, the victim’s device was infected with a miner and ClipBanker, which is malware that replaces cryptocurrency wallet addresses in the clipboard, in place of Microsoft goods. The complete study may be read on our Securelist blog, including details about the infection scheme.
Malicious TookPS installer disguised as legitimate software
Cybercriminals are not restricted to GitHub and SourceForge. Another recent scenario that our specialists discovered was hackers using phony websites that offered free downloads of specialized software to spread the harmful TookPS downloader, which we were previously familiar with via the phony DeepSeek and Grok clients. The attack was not limited to home users; it also targeted professional freelancers and businesses, since we found a number of websites that provided users with cracked versions of well-known professional software, including UltraViewer, AutoCAD, SketchUp, and others. The names Ableton.exe and QuickenApp.exe, which were allegedly versions of the well-known music production and money management programs, were among the other malicious files found.
Through devious methods, the installer downloaded Backdoor.Win32.TeviRat and Backdoor.Win32.Lapmon to the victim’s device. To learn the precise method by which the virus was installed on the victim’s device, see another Securelist post. The attackers had complete access to the victim’s computer thanks to the malware.
How to protect yourself?
Prevent downloading software that has been pirated. In any case. Never. Although a cracked program can seem alluringly free and instantaneously accessible, the cost will be expressed in data — your data — rather than cash. And no, it doesn’t imply pictures of the family and conversations with friends. Your account passwords, payment card information, cryptocurrency wallets, and even your computer’s resources for cryptocurrency mining are all targets for cybercriminals.
We suggest the following guidelines for anyone using GitHub, SourceForge, and other software portals.
- Use trial versions or substitutes rather than cracked software if you are unable to purchase the complete edition of an application. At least your device is assured to be safe, even if you don’t get to use it to its full potential.
- Download software only from reliable sources. Even so, you should exercise caution and run an antivirus program on all downloaded files, as demonstrated by SourceForge and GitHub practices.
- Use trustworthy tools to safeguard your banking information and cryptocurrency. Virtual wallets should be treated with the same respect as real ones.
Want to Study Cybersecurity?

Did you ever get interested in learning varied fundamentals of Cybersecurity right from scratch? If yes, then this is your chance! Craw Security is offering world-class options to learn 1 Year Cybersecurity Diploma Course Powered by AI through Craw Security, the Best Cybersecurity Training Institute in India, to deliver the cybersecurity best practices through international-standard training patterns by highly qualified training professionals.
To get more info regarding the upcoming batches or any other crucial details, kindly give us a call at our 24X7 hotline mobile number +91-9513805401 and have a word with our superb educational counselors.
















