What are File Upload Vulnerabilities? | Craw Security

What are File Upload Vulnerabilities? | Craw Security
What are File Upload Vulnerabilities?
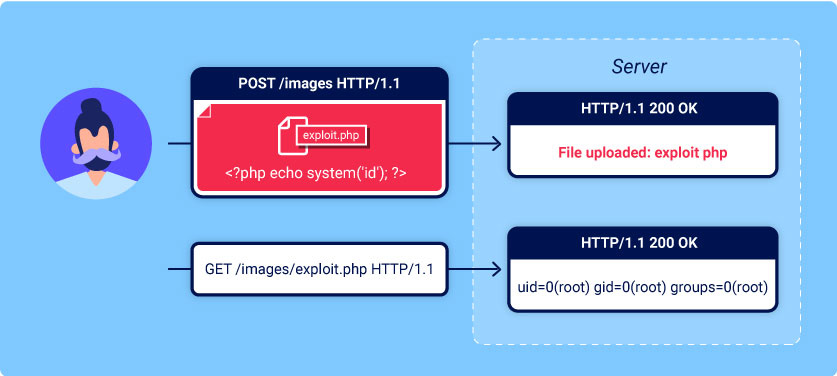
An attacker can upload harmful files into the upload capability of a web application through a file upload vulnerability, also known as unlimited file upload. If a validation limitation is not appropriately enforced, even a simple image upload feature may be used to upload random and maybe harmful files. Even script files on the server side that provide remote code execution may fall under this category.
The applications are significantly in danger from uploaded files. Getting some code into the system to be attacked is often the initial stage of an attack. All the attack has to do is figure out how to get code to run. The first is accomplished by the attacker using a file upload heap.
How do file upload vulnerabilities arise?
File upload vulnerabilities occur when web applications or systems neglect to incorporate adequate security protections for user file uploads.
There exist several prevalent factors that contribute to the occurrence of file upload vulnerabilities.
- Lack of file type validation:
A frequently seen error is the inadequate validation of uploaded file types. In the event that an application fails to verify the file type by considering both the file extension and its content, there exists a potential vulnerability whereby an adversary might potentially upload a file of a harmful kind or contain executable scripts.
- Insufficient size restriction:
The failure to implement and enforce appropriate size limitations on uploaded files might result in the occurrence of denial-of-service attacks.
- Inadequate file name sanitization:
If an application fails to adequately sanitize file names, it may become susceptible to security breaches involving the use of special characters or path traversal techniques. This scenario may give rise to complications such as the overwriting of pre-existing files or the inadvertent access of files located in undesired folders.
- Weak authentication and authorization:
File upload vulnerabilities may arise when there are deficiencies in the authentication and authorization processes in place. In the event that an unauthorized individual successfully acquires access to an account endowed with upload privileges, there exists the potential for them to exploit the system.
- Bypassing client-side controls:
If an application depends on client-side controls for the purpose of enforcing restrictions on file uploads. The ease with which attackers can circumvent these safeguards is significant, as it is well-acknowledged in academic circles that client-side measures should not be regarded as the principal security method.
How to prevent file upload vulnerabilities?
The mitigation of file upload vulnerabilities necessitates the use of a combination of safe coding principles, server-side controls, and appropriate configuration.
The following are several prevalent methods for mitigating file upload vulnerabilities:
1. File type validation:
Check file extension: The file extension should be checked in order to validate that it corresponds to the anticipated kinds. It is advisable to refrain from depending on file extensions, as they are susceptible to manipulation.
Verify file content: To ensure the accuracy of the file content, it is necessary to incorporate content-based validation techniques that enable the examination of the actual content within the file. Libraries or software tools that provide the capability to examine file signatures are highly advantageous for this particular objective.
Whitelist allowed types: The whitelist feature entails the explicit definition of a set of permissible file types. Exclude any file formats that are not specifically mentioned.
2. Size restriction:
To enhance system security and prevent potential Denial-of-Service (DoS) attacks or resource depletion, it is advisable to incorporate a mechanism that imposes maximum size limits on uploaded files. By enforcing size restrictions, the system can effectively mitigate the risk of malicious actors exploiting vulnerabilities to overwhelm system resources.
Client-side and server-side validation: Client-side validation is employed to enhance user comfort by validating user input on the client’s device before sending it to the server. On the other hand, server-side validation is utilized to verify that the imposed limits are not circumvented, since it validates the user input on the server.
3. File name sanitization:
To ensure file name safety, it is advisable to implement measures that prevent users from directly specifying file names. In order to mitigate potential problems arising from special characters or path traversal, it is advisable to include a mechanism for generating secure file names on the server side.
Regular expression validation: Regular expressions can be employed to guarantee that file names adhere to predetermined patterns.
4. Authentication and authorization:
Strong authentication is a crucial aspect that guarantees the resilience of authentication processes and verifies that users possess the requisite permissions to carry out file uploads.
Role-based access controls (RBAC): The implementation of Role-Based Access Control (RBAC) is proposed as a means to enforce appropriate authorization protocols, hence restricting file upload privileges only to approved users.
5. Malicious content detection:
The proposed solution involves the implementation of antivirus scanning, wherein an antivirus system is integrated into the existing infrastructure to conduct thorough examinations of uploaded files. This process aims to identify and eliminate any potentially dangerous content present within the files prior to their storage or further processing.
File type analysis: Utilize tools or libraries that employ file type and content analysis techniques in order to identify potential security vulnerabilities.
6. Logging and monitoring:
To enhance the monitoring of file upload operations, it is recommended to establish a comprehensive logging system that captures detailed information such as the user responsible for the upload, the timestamp of the activity, and specific file data.
Monitor anomalies: Establish monitoring systems designed to identify atypical or questionable patterns associated with file uploads, subsequently generating notifications or warnings.
Conclusion
All in all, we have tried to elaborate on the mainstream functionalities of File Upload Vulnerabilities that may certainly enhance your knowledge parameters while employing these features in real-time actions. Moreover, if you wish to know more about other prominent features of information security then you may seek enrollment in the highlighted 1 Year Diploma in Cyber Security Course under the supervision of genuinely skilled, qualified, and experienced training professionals of Craw Security, the Best Cybersecurity Training Institute in India.
To know more about the same, you just need to give us a call at our 24X7 hotline mobile number +91-9513805401.