Top 10 Zero-Day Attacks | Cyber Attacks

Top 10 Zero-Day Attacks | Cyber Attacks
Top 10 Zero-Day Attacks
Introduction:
A zero-day attack refers to the exploitation of a vulnerability in software or hardware that is not yet known to the developers, hence preventing them from addressing and patching the fault in a timely manner. These attacks can do significant harm when they exploit systems that are commonly perceived as being secure.
Moreover, this article provides an overview of 10 prominent instances of zero-day attacks in the field of cybersecurity.
1. Stuxnet
The Stuxnet worm, which was first identified in 2010, is a highly advanced computer program that took use of several previously unknown software flaws. Its primary objective was to infiltrate and disrupt Iranian nuclear facilities. The disruption has a substantial impact on the procedures involved in uranium enrichment.
2. Operation Aurora

In the year 2009, a meticulously planned assault, commonly referred to as “Operation Aurora,” was executed with the aim of targeting numerous prominent corporations, among them Google. The objective was to obtain unauthorized entry into the accounts of those advocating for human rights.
3. Heartbleed
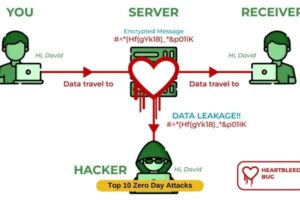
The Heartbleed bug, which was discovered in 2014, constituted a vulnerability inside the OpenSSL cryptographic package. The vulnerability had the potential to enable unauthorized individuals to access encrypted memory, so compromising confidential information.
4. Shellshock

The Shellshock vulnerability, discovered in 2014, targeted UNIX-based operating systems by exploiting vulnerabilities present in the Bash shell. This vulnerability enabled malicious actors to execute commands of their choosing.
5. Petya and NotPetya

In the years 2016 and 2017, a series of ransomware attacks were identified, wherein zero-day vulnerabilities were used to encrypt the data of affected users, afterward demanding payment for their release.
6. WannaCry

The WannaCry ransomware, which emerged in 2017, specifically exploited a previously unknown vulnerability in Microsoft Windows operating systems. This cyberattack had a global impact, impacting numerous computer systems and coercing victims into paying ransom in the form of Bitcoin.
7. Equifax Breach

The exploitation of a vulnerability in Apache Struts in the year 2017 resulted in a significant data breach at Equifax, which compromised the personal information of more than 147 million individuals.
8. Sandworm

Discovered in the year 2014, the zero-day attack in question specifically targeted the Windows operating system and was found to be associated with the BlackEnergy virus. This malicious activity resulted in power disruptions within Ukraine.
9. JailbreakMe 3.0

In the year 2011, an instance of a zero-day vulnerability in Adobe PDF was successfully exploited, hence enabling users to do a jailbreak on their iOS devices without the need for a computer connection.
10. Kerberos Golden Ticket
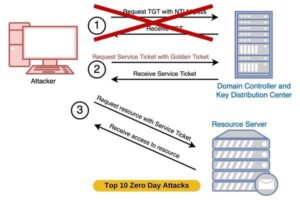
In the year 2014, a zero-day vulnerability in the Kerberos Ticket Granting Ticket mechanism was discovered, which let attackers gain unauthorized access to any service or user within the Active Directory domain.
Conclusion
In a nutshell, we would love to comment that there were several zero-day attacks in the past that highlighted the imperative for maintaining a state of constant attention and implementing proactive defense measures within the realm of cybersecurity. They serve as a reminder that no system is entirely invulnerable, emphasizing the importance of implementing a combination of regular upgrades, monitoring, and adherence to proper security standards in order to effectively prevent prospective breaches.
Moreover, if you have a keen intention to learn more about the other types of Zero-Day Attack methodologies and the prime approaches to avert them, then you can join a genuine cybersecurity training institute in India, like Craw Security, the Best Cybersecurity Training Institute in India. Call +91-9513805401 to know more about the upcoming batches and other relevant information.

















