Best Web Application Security Course in Delhi | Craw Security
June 11, 2021 2024-12-17 13:13Best Web Application Security Course in Delhi | Craw Security
Web Application Security Course in Delhi | Web Application Penetration Testing Course
Bestseller
3571 Student Reviews
The varied methodologies employed by Security Analysts to safeguard a particular website or web application by a means of a predefined set of algorithms is known as Web Application Security. The main objective of Web Application Security is to secure a particular target web application from malicious entities or actors.
- Course Duration : 60 Hours
- Language : Hindi | English
- Course Delivery : Online | offline

FutureSkills Prime Partner (A MeitY NASSCOM Digital Skilling Initiative)
Accredited by NASSCOM, approved by the Government of India
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
What will you learn in the Best Web Application Security Training in Delhi?
Firstly, in this genuine Web Application Penetration Testing Course, one can dedicatedly find some authentic course modules and the fundamentals related to the Web Application Security Course for an in-depth understanding. In addition, this can be done with the help of huge experienced teachers and mentors group that can literally transform a basic individual into a high-tech expert candidate fully capable of doing multiple assignments associated with Web Application Security Course protocols.
However, students join this Web Application Security Certification for varied reasons including safeguarding their own website(s) for good or else joining any authentic MNC in the near future for a fantastic career ahead. The institutions of Craw Security at Saket and Laxmi Nagar locations in Delhi provide a sincere approach in Web Security Course for a long-lasting study experience of our students suffering a tough time in finding the right kind of career guidance for a balanced future ahead.
Web Application Security Course Content
Lesson 01: Networking and protocol
Lesson 02: HTTP & HTTPS
Lesson 01: Briefing about various frameworks
Lesson 02: Explaining the OWASP top 10
Lesson 01: Subdomains enumeration
Lesson 02: Domains filtration
Lesson 03: Endpoints enumeration
Lesson 04: Grepping responses
Lesson 01: Union based SQLI
Lesson 02: SQL Authentication Bypass
Lesson 03: Error based SQLI
Lesson 04: Time-based SQLI
Lesson 05: In-band and out-of-band SQLI
Lesson 06: Create our own script to automate the process of Blind SQLi
Lesson 01: DVWA source code review
Lesson 02: PHP command injection with various functions
Lesson 03: Filter bypass
Lesson 01: Cookie hijacking
Lesson 02: HSTS policy bypass
Lesson 01: Protection by pass
Lesson 01: Filter bypass
Lesson 02: Server-side configuration check
Lesson 01: Explaining JavaScript
Lesson 02: Reflected JavaScript
Lesson 03: Stored JavaScript
Lesson 04: DOM-based JavaScript
Lesson 01: UUID protection
Lesson 01: GIT source code disclosure
Lesson 02: Client-side source code review
Lesson 01: Template engine Explaining
Lesson 02: Various exploitation techniques with various Template engine
Lesson 01: Brute-force attacks
Lesson 02: Creating wordlists
Lesson 03: Logic errors bypass
Lesson 01: Explaining HTTP/1.1 and HTTP/2
Lesson 02: CL-TE attack
Lesson 03: TE-CL attack
Lesson 04: TE-TE attack
Lesson 01: Whitelisting and blacklisting
Lesson 02: Bypassing blacklisting
Lesson 03: Brief on regex
Lesson 01: Traversal payload
Lesson 02: Bypass WAF
Lesson 03: Reading and inclusion difference
Lesson 01: Path traversal payload to read the file
Lesson 01: Explaining HTML web page
Lesson 02: Reflected HTML injection
Lesson 03: Stored HTML injection
Lesson 01: Apache config brief
Lesson 02: Host header Explaining
Lesson 01: POST method explain
Lesson 02: Encoded POST method
Lesson 03: Various headers related to file upload
Lesson 01: JWT tokens algorithms
Lesson 02: Brute force on HS256 algo
Lesson 03: Logic error bypass
Lesson 01: Introduction to database
Lesson 02: Install MySql
Lesson 03: Explain basic query of sql
Lesson 04: Connection with python
Lesson 05: Execute some queries by python
Lesson 01: XXE vulnerability to cause DOS
Lesson 02: Business logic to cause DOS
Lesson 01: POC ( proof of concept)
Lesson 02: Executive and Management Report
Lesson 03: Technical Report For IT and security Department
Web Application Security Our Course Advisor
Web Application Security Course | Web Pentesting Course
With the trending technology of the technological world, we need proper security for our websites from the ill-eyes of potential black hat hackers who want to steal crucial and sensitive datasets from them. Moreover, one can learn the OWASP Top 10 common cyber security attacks and Web Application Security from the high-end institutions of Craw Cyber Security at Saket and Laxmi Nagar providing source-rich content in the corresponding curriculum of Web Application Security Course. These kinds of Application Security Certification Courses are highly recommended to the personnel devotedly associated with Web Designing and Development who have a keen interest in safeguarding their own developed website from the evil intentions of data hackers sitting anywhere in the world. Craw Cyber Security Insitute at Saket and Laxmi Nagar offer a quality Web Application Security Course in Delhi. This prominent training of the Best Application Security Certification covers numerous major and minor topics like SQL Injection, XSS, Php Injection, CSRF, Indirect object reference, etc.In this distinguished Web Application Security Training in Delhi, one will understand how the heinous OWASP Top 10 Threats may be mitigated.
Key Specifications
- Basics of Web Applications
- BURPSUIT / Proxy Interception
- How to inject SQL injection
- Vulnerabilities in Web Application and how to remove them
- How to manage Data Breach
- Buffer overflow
- Cross-Site Request Forgery
- How to apply design and coding
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
Web Application Security Course Description
In the majors of this magnificent Web Application Security Course, one will understand the OWASP Top 10 Threats that can literally give troubles to many Web Security Analysts. Apart from that, this splendid Web Application Security Training Course will enhance your chances of getting placed in major IT organizations willing to recruit permanent staff for safeguarding their websites from being compromised via illicit hacking.
Furthermore, the Web Application Security Course will broaden your knowledge quotient regarding all the major and minor security challenges that a security analyst face on one’s day-to-day official chores. Craw Cyber Security Institute’s main USPs comprises giving prominent education related to the fundamentals of Web Application Security Course to the advanced level.
One can truly understand all the educational material offered in the Web Pentesting Course through our vast and dedicatedly verified curriculum of Web Application Security Course having a rich subject matter Web Application Security Course Syllabus for all-round development of the students.
In addition, the Best Application Security Certification will certainly assist you to search all the problems and threats in Web Applications and the distinguished methodologies to remove these Vulnerabilities concerning Web Applications. Craw Security is a worldwide trustworthy brand in the distinguished domains of Information security and Web Application Security Course Training in Delhi with a valid certificate from the establishment after the successful completion of the Web Application Security Course.
Craw Security's Students Awarded











Web Application Security Course Online with Certification
In Web Security Course from Craw Security offers various aspects where one person has to go through several fundamentals of Web Security Testing, OWASP Testing, Backtrack & Kali, Advanced Web Application Security Testing, Web Application Firewall (Mod Security), etc.
Craw Cyber Security Institute recently introduced a virtual, interactive, and engaging platform to offer hands-on training in Web Application Security Course’s testing methodologies. Since we have an abundance of traffic for this particular training of Web Application Security Course, a Web Application Security Course Online has been started with all prerecorded high definition videos possessing all needful content that can be a proven source of knowledge to all those candidates who want to learn this splendid course at one’s pace.
Related Cyber Security Course
Latest Blogs
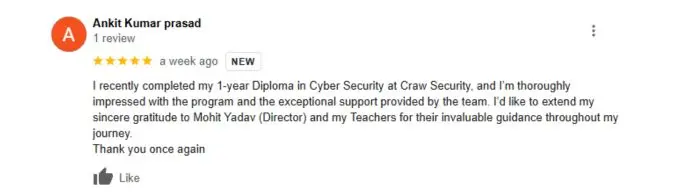
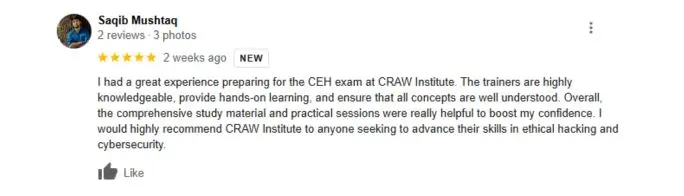
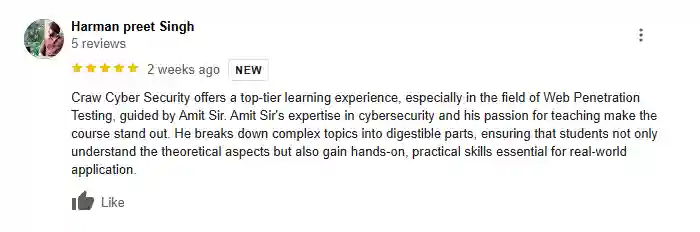
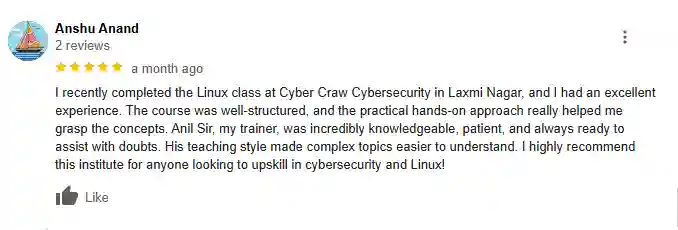
What People Are Saying About Craw Security
Google Review (2,549) ★★★★★

Web Application Security Frequently Asked Questions
The varied methodologies employed by Security Analysts to safeguard a particular website or web application by a means of a predefined set of algorithms is known as Web Application Security. The main objective of Web Application Security is to secure a particular target web application from malicious entities or actors.
Some of the major issues that arise in securing a Web Application are as follows:
- Injection Attacks
- Broken Authentication
- Cross-Site Scripting (XSS)
- Insecure Direct Object
- References (IDOR)
- Security Misconfigurations
- Unvalidated Redirects and Forwards
- Missing Function Level Access Control
Any practicing Web Security Analyst can genuinely employ a series of exercises to confirm the security parameters of a web application. Some of the major Web Application Security parameters are as follows:
- Maintain Security During Web App Development
- Be Paranoid: Require Injection & Input Validation
- Encrypt your data
- Use Exception Management
- Apply Authentication, Role Management & Access Control
- Don’t Forget Hosting/Service-Focused Measures
- Avoid Security Misconfigurations
- Implement HTTPS (and Redirect All HTTP Traffic to HTTPS)
- Include Auditing & Logging
- Use Rigorous Quality Assurance and Testing
- Be energetic to Keep Up With the Malicious Actors
The diverse kinds of application security comprise many features including authentication, authorization, encryption, logging, and application security testing. Many Web Developers also code their applications during the development process to reduce the security risks and vulnerabilities.
The corresponding security vulnerabilities in the web application if found by any malicious actors then can perform a series of cyberattacks on those web applications using those vulnerabilities. A potential attacker can gain access to a lot of sensitive information encrypted in the server of the corresponding target web applications.
A web application (or web app) is application software that runs on a web server, unlike computer-based software programs that are run locally on the operating system (OS) of the device. Web applications are accessed by the user through a web browser with an active network connection.
You can literally learn the fundamentals of the Web Application Security Course in Delhi from the verified and accredited institutions of Craw Cyber Security at Saket and Lakshmi Nagar locations.
The various fundamental concepts related to the Web Application Security Course comprises in the corresponding curriculum associated with Web Pentesting Course. For instance, one dedicated aspirant will learn concepts like data modeling and database technologies, the web server environment and middleware components, network protocols, the user interface, and basic visual design and user interaction methodologies within the curriculum of the Web Application Security Course.
It is a type of Cyber Attack done by a potential hacker using a shred of information related to SQL (Structured Query Language) code to manipulate the datasets and have the access to crucial info containing some sensitive piece of personal information that be very tricky for an organization to lose.
The primary aim of the course is to educate developers, designers, architects and organizations about the consequences of the most common web application security vulnerabilities and methodology to protect against such vulnerabilities
Advanced Web Attacks and Exploitation (WEB-300) is a high level web application security survey course. We instruct the abilities expected to direct white box web application infiltration tests.
SECURITY TESTING is a type of SoftwareTesting that uncovers vulnerabilities, threats, risks in a software application and prevents malicious attacks from intruders.
Certainly! A web application security course is important for a variety of reasons:
- Rising Cyber Threats,
- Critical Data Protection,
- Regulatory Compliance,
- Building Trust,
- Economic Considerations,
- Technical Excellence,
- Broadening Skill Set,
- Proactive vs. Reactive,
- Complex Web Ecosystems,
- Evolution of Web Technologies, etc.
The primary topics that are covered in this course are as follows:
- Module 01: Introduction
- Module 02: Owasp top 10
- Module 03: Recon for bug hunting
- Module 04: Advanced SQL injection
- Module 05: Command injection
- Module 06: Session Management and Broken Authentication Vulnerability
- Module 07: CSRF – Cross-Site Request Forgery
- Module 08: SSRF – Server Site Request Forgery
- Module 09: XSS – Cross-Site Scripting
- Module 10: IDOR – Insecure Direct Object Reference
- Module 11: Sensitive Data Exposure and Information Disclose
- Module 12: SSTI – Server Site Template Injection
- Module 13: Multi-Factor Authentication Bypass
- Module 14: HTTP Request Smuggling
- Module 15: External Control of File Name or Path
- Module 16: LFI – Local File Inclusion and RFI – Remote File Inclusion
- Module 17: Source Code Disclosure
- Module 18: Directory Path Traversal
- Module 19: HTML Injection
- Module 20: Host Header Injection
- Module 21: SQL Authentication Bypass
- Module 22: File Upload Vulnerability
- Module 23: JWT Token Attack
- Module 24: Security Misconfiguration
- Module 25: URL Redirection
- Module 26: Flood Attack on Web
Taking a Web Application Security Course can offer numerous benefits, both in your current job role and for future opportunities. Here’s how it can provide awesome results:
- Enhanced Skill Set,
- Job Security,
- Increased Job Opportunities,
- Career Advancement,
- Credibility & Recognition,
- Broadened Role,
- Risk Mitigation,
- Effective Communication,
- Potential for Consultancy,
- Financial Benefits,
- Continuous Learning,
- Preparedness for Future Tech, etc.
List of Companies you can get placements in









