Learn Internet of Things IoT Pentesting Course in Delhi
October 10, 2021 2025-03-30 11:16Learn Internet of Things IoT Pentesting Course in Delhi
Internet of Things Penetration Testing with AI in Delhi | Internet of Things Pentesting Course
Bestseller
1900+ Student Reviews
With the help of the most committed and passionate instructors and mentors with years of experience and top-notch subject matter expertise, the Best IoT Training Institute in Delhi offers its best-in-class IoT Certification Course. Learn the real Internet of Things Penetration Testing with AI. Through engaging live classroom sessions and an online IoT course, one can grasp all the basic ideas related to the Internet of Things course details and learn from a knowledgeable team of working professionals who give high-quality knowledge.
- Course Duration : 60 Hours
- Language : Hindi | English
- Course Delivery : Online | offline

FutureSkills Prime Partner (A MeitY NASSCOM Digital Skilling Initiative)
Accredited by NASSCOM, approved by the Government of India
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401
What would you learn in the Internet of Things Pentesting Course?
Our highly qualified trainers and mentors provide a top-notch Internet of Things Pentesting Course through an authentic and highly interactive curriculum that has been duly vetted and approved by numerous acknowledging bodies. This ensures that the course is completed on time.
Several processes in our high-end IoT Course in Delhi involve our security researchers and analysts breaking into the many systems and gadgets with the attitude of an attacker, exactly like a would-be hacker.
As a result, it highlights any potential security flaws, dangers, and weaknesses that could result in an IoT device security breach if they fall into the wrong hands. All of the core principles related to IoT Penetration Testing with AI are covered in the upscale Internet of Things Pentesting Course offered by Craw Cyber Security Institute at its cutting-edge facilities in Saket and Laxmi Nagar.
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401
Internet of Things Penetration Testing Course Content
Lesson 01: What is IOT?
Lesson 02: Why is IoT important?
- Use AI tools to automate vulnerability scanning in IoT devices by analyzing traffic patterns and identifying anomalies or weak points,
Lesson 01: How does IOT work?
Lesson 02: Advantages & Disadvantage’s
Lesson 01: Explanation
Lesson 02: Use of sensor with example
Lesson 01: Explanation
Lesson 01: What is radio wave?
Lesson 02: Radio Frequency Spectrum band
Lesson 03: Explanation
Lesson 01: Difference type of protocols
Lesson 03: Explanation
Lesson 01: Explanation
Lesson 01: Explanation
Lesson 01: Explanation
Lesson 01: Explanation with practical
Explanation with practical
Lesson 01: Explanation
Lesson 01: Explanation with practical
Lesson 01: Usage of firmware for penetester
Lesson 02: What is it?
Lesson 03: Extracting squashfs file system from file system
Lesson 04: How to obtain firmware?
Lesson 05: Explanation with practical
Lesson 01: Explanation
Lesson 01: Explanation with practical
Lesson 01: Explanation
Lesson 01: Explanation
Lesson 01: Explanation
Lesson 01: Explanation
Talk to Our Course Advisor
AI-Based Internet of Things Course Syllabus | IoT Training in Delhi
Our quantitative approach consistently strives to provide our students who wish to learn from the most experienced mentors and top-notch teaching faculty with as many high-quality AI-based Internet of Things course details as possible. This will allow them to effectively address any questions they may have about the course syllabus.
In addition, Craw Security makes a sincere effort to hire top-tier mentors and trainers to provide our students with the Best IoT Course in Delhi so they can succeed. This allows them to interact face-to-face with prestigious IT companies’ hiring managers, who are all confident during the interview process.
Key Features of Internet of Things Pentesting Course in Delhi:
- Analytic Engine for IoT
- Scope of the penetration testing engagement.
- What are your biggest fears regarding security of your solution.
- Your organization’s current security posture.
- Overview of Why IoT is so important
- Machine learning for intelligent IoT
- Introduction to Mobile app platform & Middleware for IoT
- Expected time duration and financials.
- Explaining about our penetration testing methodology for your product.
- Conceiving a new IoT product- Product Requirement document for IoT
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
IoT Penetration Testing Application Security Course Description
In order to leave a lasting impression on the minds of its students, the institutions at Craw Security’s Saket and Laxmi Nagar locations are committed to offering some of the Best Internet of Things Certification Courses.
Additionally, Craw Cyber Security Institutions provides a comprehensive security assessment and the Best IoT Course in Delhi NCR that eliminates the fundamentals of penetration testing through our exclusive offering of Attacker Simulated Exploitation for genuine IoT solutions, all with the assistance and support of its elite delegation of knowledgeable trainers and mentors.
We frequently focus on some special methods of exploitation, such as combining less important vulnerabilities to create a prime compromise, even though in some of the well-known situations the devices have the same kinds of vulnerabilities.
Just to ensure the study of the IoT Certification Course goes to every worthy and interested individual, Craw Security delivers superb quality AI-based Internet of Things Certification Course Online that provides access to many users to learn at their own pace while working as a professional individual at their reputed organization.
Further, we provide a genuine Online IoT Course in Delhi with nice and sincere planning in order to prove all the worthiness of our Internet of Things-based studies for all the interested participants. Learners can opt for a favorable time slot throughout the provided timings to learn the varied fundamentals of the AI-based IoT Pentesting Course by Craw Security, the Best Cybersecurity Training Institute in India.
There are very many institutes in the wild that provide a favorable environment for their students to flourish flawlessly in order to get their maiden jobs in the IT security industry. In this context, Craw Security is one of the premier IoT Training Institutes in Delhi NCR that provides “100% Placement Assistance” to the learners who genuinely finish our practical training of AI-based Internet of Things Pentesting Course along with a bigger vision to perform in mainstream IT companies in the competitive job market.
Second, candidates will have access to a number of job openings at Craw Security, the Best IoT Training Institute in Delhi. Companies are searching for developers with shared expertise in this subject because of the industry’s rapidly growing demand for IoT developers.
Furthermore, IT businesses prefer to hire assets rather than liabilities, so they often no longer prioritize hiring students with a wealth of skills, potential, and subject expertise. Regardless of any other aspect we provide during our interactive live classroom sessions, companies will always give preference to candidates who have some experience working on live projects and an in-depth understanding of the field.
Craw Security's Students Awarded











Who should do the Internet of Things Pentesting Course?
This amazing Internet of Things Pentesting Course in Delhi is open to a wide range of individuals, including the following:
- Anyone has a strong desire to create IoT devices for trade, personal use, official functions, or even college projects.
- Professionals in cyber security who are interested in learning more about protecting the entrance and endpoints of various end-user devices, such as laptops, desktop computers, cellphones, tablets, etc.
Related Cyber Security Course
Latest Blogs
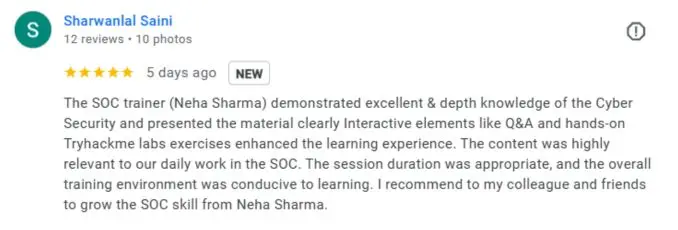
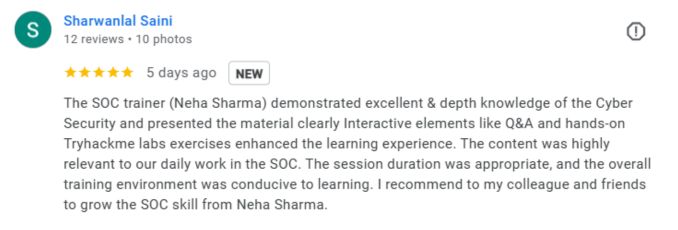
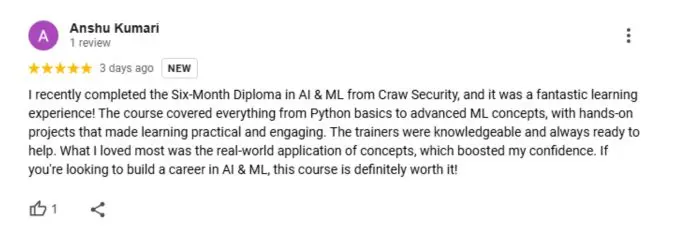
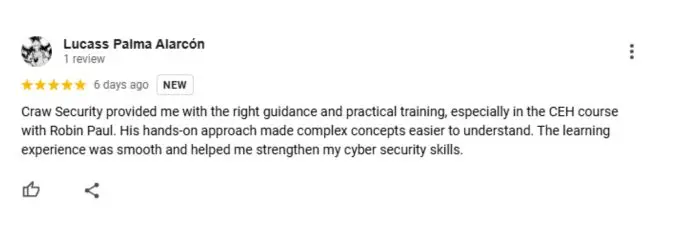
What People Are Saying About Craw Security
Google Review (1900+) ★★★★★
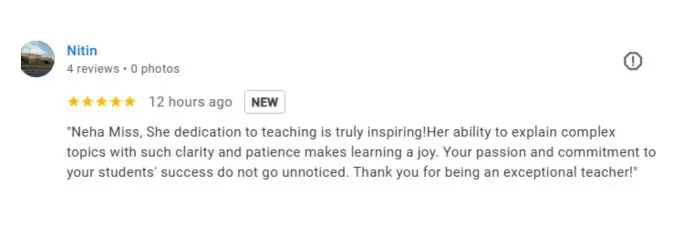
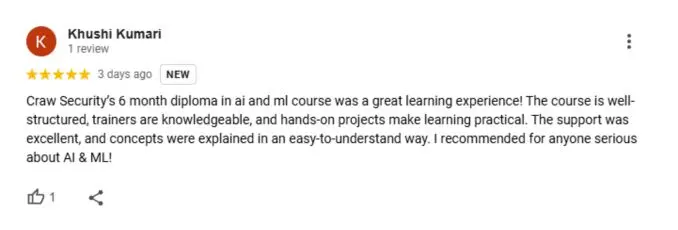
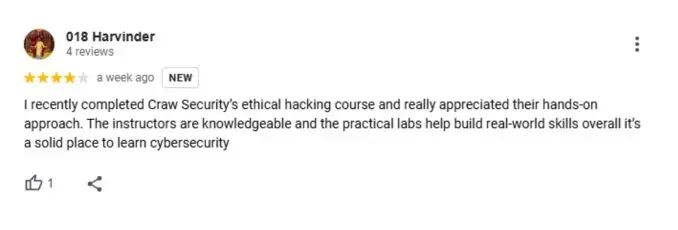
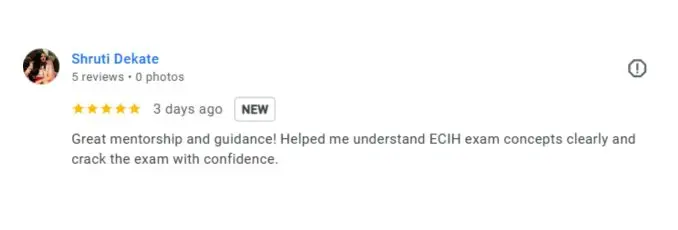
IoT Penetration Testing Frequently Asked Questions
A simulated cyberattack against a system is used in IoT penetration testing, also known as a pen test, to check for any potential risks, weaknesses, breaches, or vulnerabilities. The penetration test’s insights can be applied to repair vulnerabilities found and improve WAF security settings.
The 5 most dedicated stages or levels associated with IoT Penetration Testing with AI are mentioned below:
- Planning and reconnaissance,
- Scanning,
- Gaining System Access,
- Persistent Access, and
- The Final Analysis/ Report.
The following are a few of the top penetration testing tools that are necessary for carrying out the various IoT pentesting testing techniques:
- Appknox
- AWS IoT Device Defender
- Verimatrix
- Palo Alto Network
- Entrust
IoT security is the process of protecting end-user devices, including laptops, desktop computers, tablets, smartphones, smart devices, and other all-encompassing gadgets.
The following table lists the main distinctions between a computer system and an Internet of Things device:
IoT Devices | Computer System |
IoT devices are unique-objective devices. | Computers are general-objective devices. |
IoT devices can only perform a special function for which it is scheduled. | Computers can perform multiple functionalities. |
That specific function is made possible by the hardware and software that are integrated into the specific IoT devices. | The computers’ integrated hardware and software enable the completion of numerous tasks at once (e.g. calculation, video streaming, gaming, etc.). |
Because IoT devices are made and built to do a certain function, they may be faster and less expensive than PCs at that particular task. | A computer is costly worse as slower at a specific function in comparison to an IoT device. |
e.g.: Music Players- iPod, Alexa, smart cars, etc. | Examples: Desktops, Laptops, etc. |
IoT Penetration Testing with AI is the process of breaking into certain internet-based end-user devices, including desktops, laptops, tablets, smartphones, smart devices, etc., with the prospective mindset of a black hat hacker in order to find risks, vulnerabilities, hiccups, and loopholes.
Some of the famous IoT examples where we are dedicatedly using them at full throttle are mentioned below:
- Connected appliances.
- Smart home security systems.
- Autonomous farming equipment.
- Wearable health monitors.
- Smart factory equipment.
- Wireless inventory trackers.
- Ultra-high-speed wireless internet.
- Biometric cybersecurity scanners.
Yes, you are only half aware of the complete truth if you are attempting to begin a career in the broad field of penetration testing based solely on the high demand and the associated income. Even specialists with coding expertise have a busy schedule when it comes to penetration testing.
IoT Penetration Testing with AI is undoubtedly a good career choice because all major and small IT organizations are hiring permanent staff members who are in charge of the various penetration testing procedures appropriately associated with the diverse end-user devices, including laptops, computers, tablets, smartphones, smart gadgets, and many other IoT devices.
Any internet-based device may be compromised with a set of tools and methods, and a working expert with these skills can effectively identify vulnerabilities concealed inside a collection of IoT devices.
The need to do IoT (Internet of Things) penetration testing stems from various factors, with a primary focus on ensuring the security and functionality of the rapidly expanding array of IoT devices. Below is a comprehensive analysis:
- Rapid Growth of IoT Devices,
- Diverse Ecosystem,
- Inherent Vulnerabilities,
- Sensitive Data Collection,
- Potential for Physical Harm,
- Persistent Connectivity,
- Limited Update Capability,
- Infiltration Point for Larger Networks,
- Reputation and Compliance Risks,
- Complex Supply Chain, etc.
The mainstream prerequisites for enrolling in this Internet of Things Penetration Testing in Delhi by Craw Security are as follows:
- Basic Understanding of IoT,
- Networking Fundamentals,
- Programming Skills,
- Cybersecurity Basics,
- Operating Systems,
- Hardware Familiarity,
- Familiarity with Common Tools,
- Wireless Communication,
- Web Technologies,
- Willingness to Learn and Experiment,
- Ethical Considerations, etc.
The typical course duration for IoT Penetration Testing in Delhi at Craw Security is 60 hours.
Yes, you will receive a certificate from FutureSkills Prime, a MeitY – NASSCOM, Digital Skilling Initiative, after successfully completing the examination from the FSP.
The mainstream topics that will be covered in this primetime Internet of Things Penetration Testing in Delhi by Craw Security are as follows:
- Module 01: Overview of Why IoT is so important
- Module 02: Introduction of IoT
- Module 03: Introduction to Sensor Network
and Wireless protocol - Module 04: Review of Electronics Platform,
Production & cost projection - Module 05: Conceiving a new IoT productProduct Requirement document for IoT
- Module 06: Introduction to Mobile app
platform & Middleware for IoT - Module 07: Machine learning for intelligent IoT
- Module 08: Analytic Engine for IoT
- Module 09: Iaas/Paas/Saas-IoT data, platform, and software as a service revenue model
Yes, the course curriculum includes a wide range of hands-on labs or practical sessions under the prime supervision of world-class training mentors.
The highlighted job opportunities that you can pursue after completing the course are as follows:
- IoT Security Analyst,
- IoT Penetration Tester
- Security Consultant
- IoT Security Researcher
- IoT Security Solutions Architect
- Incident Responder for IoT
- IoT Security Trainer/Instructor
- IoT Security Engineer
- Compliance and Auditing
- Sales/Technical Sales in IoT Security
- Freelance IoT Security Expert
The cost of the IoT Penetration Testing Course in Delhi by Craw Security is highly affordable and can be afforded by an individual hailing from an economically weaker section of society. Hence, you don’t need to panic at all; give us a call at +91-9513805401 and seek your best price in no time.










