Best Ethical Hacking Course in Delhi, India
May 4, 2021 2025-03-29 15:50Best Ethical Hacking Course in Delhi, India
Ethical Hacking Course with AI in Delhi | Best Ethical Hacking Institute
Bestseller
3571 Student Reviews
Learn the Ethical Hacking Course with AI in Delhi from the best mentorship in town, which provides a qualitative approach towards a genuine Cyber Security Course to understand the fundamentals of the Ethical Hacking Course with AI Syllabus in a better way. Craw Security possesses a dreamtime of expert professionals who possess all the necessary resources for a better understanding of the sincere ethical hacking training and certification for the current and prospective students at Saket and Laxmi Nagar institutes.
At Craw Security, we deliver the best of ethical hacking course with AI fundamentals right from scratch to all beginners who wish to transform into a fully-fledged cybersecurity expert. Moreover, learners from almost all over the world join this proactive Ethical Hacking Course with AI to have a career guide and counseling session by Mr. Mohit Yadav, a renowned cybersecurity expert worldwide.
- Course Duration : 60 Hours
- Language : Hindi | English
- Course Delivery : Online | offline

FutureSkills Prime Partner (A MeitY NASSCOM Digital Skilling Initiative)
Accredited by NASSCOM, approved by the Government of India
Book a Trial Demo Class
Training Available 24*7 Call at 9513805401
Why would learn in Ethical Hacking Course with AI in Delhi?
There is a lot to learn in the Ethical Hacking Course with AI Syllabus, which is dedicatedly curtailed after a thorough dialogue process with world-renowned cybersecurity analysts and experts hailing from all over the world. As you can see, the value of AI and ML is highly booming in today’s world; hence, in order to upscale our students as per today’s technological advancements, Craw Security has also updated its Ethical Hacking Course with the technological advancements of AI features and characteristics.
We are experiencing a technological revolution at its best, and smart devices and self-run gadgets are taking over the world. In addition, there is a lot that can happen in this industry in the name of innovation in the near future as well. Since all the things have gone to the cloud servers using a suitable data connection, hackers have a potential mindset to steal all the confidential and safe datasets stored on the cloud servers.
To compete for this, organizations need a permanent team of white hat hackers that can track down all the issues and concerns. There are multiple institutes in the market that provide the Best Ethical Hacking Course Only With Certificate as well as a proper training module to understand the fundamentals of cyber security through more specified methods. In this context, students with the best minds can start this genuine Ethical hacking Course with AI in Delhi at once without any further delay to get the best start in the field of information security right under the guidance of Mr. Mohit Yadav and other best cybersecurity faculty members in India.
Book a Trial Demo Class
Training Available 24*7 Call at +91 9513805401

Introduction of AI in Ethical Hacking Course
Craw Security’s Ethical Hacking Course is a wonderful way to learn about artificial intelligence or AI. Enrolling in this course will enable those who are keen to work as ethical hackers to become outstanding cybersecurity experts who have a high level of tolerance for AI-based concepts and can apply a range of ethical hacking techniques in practical situations.
For those who wish to start a successful career in the Ethical Hacking Course with AI foundations, Craw Security, the Best Cyber Security Training Institute in Delhi NCR, offers an excellent choice: the Ethical Hacking Course with AI. Give our outstanding educational counselors a call at +91-9513805401 right now to find out what the best part of an educational counseling session is.
Practical Ethical Hacking Course with AI Objectives
During this highly hands-on Ethical Hacking Course with AI, we will deliver the following factors to all the participating individuals:
- An Ethical Hacker’s Day in the Life. What is the daily routine of an ethical hacker? What is their earning potential? What kinds of evaluations may an ethical hacker conduct? We’ll answer these and other questions.
- Note-taking that works. The quality of an ethical hacker is determined by the notes they keep. We’ll go over several essential note-taking skills that can help you succeed in the course and in your career.
- A refresher on networking. The ideas of computer networking are the main topic of this section. The OSI model, subnetting, common ports and protocols, and even a network constructed with Cisco CLI will all be covered.
- Hacking Techniques. As the course goes on, we will delve deeper into the five stages of hacking, which are summarized in this section.
- Reconnaissance and Information Gathering. You will discover how to use open-source intelligence to find information about a client. Even better, you’ll discover how to use Burp Suite to collect data, locate subdomains during client engagements, and extract compromised credentials from databases to carry out credential-stuffing attacks.
- Scanning and Enumeration. The skill of enumeration is one of the most crucial subjects in ethical hacking. You will discover how to find open ports, investigate possible weaknesses, and acquire a variety of tools required for high-quality enumeration.
- Fundamentals of Exploitation. You’ll make use of your first machine here! We’ll learn how to do brute force and password spraying assaults, how to manually exploit systems using coding, how to use Metasploit to obtain access to machines, and much more.
- Capstone for the mid-course. Everything you have learned thus far is put to the test in this section, which presents you with ten vulnerable boxes that get harder and harder. Along the journey, you will discover new tools and ways of thinking, as well as how an attacker thinks. Do you possess the necessary skills?
- Active Directory. Did you know that Active Directory is used in the environments of 95% of Fortune 1000 companies? Because of this, one of the most crucial things you should learn—and one of the least taught—is Active Directory penetration testing. The course’s Active Directory section covers a number of subjects. You will learn how to hack Active Directory and set up your own lab. Token impersonation, pass-the-hash/pass-the-password, GPP assaults, golden ticket attacks, IPv6 DNS takeovers, SMB relays, LLMNR poisoning, and many more are examples of attacks. Important tools like PowerView, Bloodhound, and mimikatz will also be taught to you. You shouldn’t skip this section!
- After Exploitation. This article discusses the fourth and fifth phases of ethical hacking. After we have taken advantage of a machine, what do we do? How are files transferred? How can we change course? Which procedures work best for cleaning up and preserving access?
- Web Application Penetration Testing. The art of enumeration is reviewed in this section, along with a number of new tools that will facilitate the process. Additionally, you will discover how to use Bash scripting to automate these programs. The course delves into the OWASP Top 10 following the enumeration portion. We will do walkthroughs utilizing vulnerable online applications and go over attacks and countermeasures for each of the top ten. SQL Injection, XML External Entities (XXE), Sensitive Data Exposure, Security Misconfigurations, Cross-Site Scripting (XSS), Insecure Deserialization, Using Components with Known Vulnerabilities, and Inadequate Logging and Monitoring are among the topics covered.
- Wireless Assaults. In less than five minutes, you will discover how to breach a wireless network and launch wireless attacks against WPA2.
- Report Writing and Legal Documentation. We will explore the legal documents that you can come across as a penetration tester, such as Master Service Agreements, Rules of Engagement, Non-Disclosure Agreements, and Statements of Work. This is a topic that is rarely discussed. We’ll talk about report writing as well. A sample report and a walkthrough of a report from a real customer evaluation will be given to you.
- Career Guidance. Career advice and finding a job in the field are covered at the course’s conclusion.
- A Good Exposure To AI Fundamentals. Participants will certainly have a better understanding by gathering good information about AI-based fundamentals right under the supervision of world-class training professionals with many years of classic work experience in shaping many lives of students with their best piece of ethical hacking training with full AI exposure.
You will have a thorough understanding of wireless penetration testing, web application penetration testing, and external and internal network penetration testing by the end of this course. Every lesson is based on practical experience and what has been encountered during real-world field engagements.
Ethical Hacking Course After 12th: Eligibility
The prominent Ethical Hacking Course with AI is the key source to understand all the needful course content required to extract the crucial knowledge related to information security to safeguard the corresponding websites, and/or the IT infrastructure of the target organization.
This primary knowledge possessing Ethical Hacking Course For Beginners can benefit anyone who is devotedly searching for a perfect reference point to start one’s career trajectory in this magnificent domain of information security.
A Sincere Curriculum of Ethical Hacking Course with AI in Delhi
The modules utilized in imparting the decent Ethical Hacking Course with AI in Delhi by Craw Security are as follows:
Lesson 01: Intro To Ethical Hacking
Lesson 02: Types of Attacks
Lesson 03: Hacking Methodology
Lesson 04: Cyber Kill Chain
Lesson 05: Types of Attackers
Lesson 06: CIA Traid
Lesson 07: Risk Management
Lesson 08: Cyber Laws
Lesson 01: What is Active Footprinting
Lesson 02: Different kinds of information gathered in Footprinting
Lesson 03: Tools for Active Footprinting = nmap, hping, masscan
Lesson 01: What is Active Footprinting
Lesson 02: Different kinds of information gathered in Footprinting
Lesson 03: Tools for Active Footprinting = nmap, hping, masscan
Lesson 01: What is passive footprinting
Lesson 02: Footprinting Through Whois
Lesson 03: Footprinting Through Website / Web Services
Lesson 04: Footprinting Through search engine
Lesson 05: Footprinting Through DNS
Lesson 06: Footprinting Through Email
Lesson 07: Footprinting Through Network
Lesson 08: Footprinting Through Social Media
Lesson 09: Tools for Passive Footprinting – Google dorks, shodan, netcraft
Lesson 01: Overview of Network Scanning
Lesson 02: Scanning Methodology
Lesson 03: Host Discovery
Lesson 04: Port Scanning Techniques
Lesson 05: Scanning tools – nmap, netdiscover, arp-scan -1
Lesson 01: Enumeration Concepts
Lesson 02: NetBIOS Enumeration
Lesson 03: SNMP Enumeration
Lesson 04: LDAP Enumeration
Lesson 05: SMTP Enumeration
Lesson 06: DNS Enumeration
Lesson 01: Authentication
Lesson 02: Gaining Access
Lesson 03: Password cracking
Lesson 04: Password Cracking Techniques
Lesson 05: Steganography
Lesson 01: Introduction to Malware
Lesson 02: Types of Viruses
Lesson 03: Types of Worms
Lesson 01: Types of Trojans
Lesson 02: Components Of a Trojan
Lesson 01: Introduction to Botnets
Lesson 02: Characteristics of Botnets
Lesson 01: Introduction to Ettercap and Bettercap
Lesson 02: Practical on Ettercap
Lesson 03: Practical on Bettercap
Lesson 01: Introduction to Wireshark
Lesson 02: Practical on Wireshark
Lesson 01: Types of Social Engineering Attacks
Lesson 02: Human Based Social Engineering Attacks
Lesson 03: Computer Based Social Engineering Attacks
Lesson 04: Mobile Based Social Engineering Attacks
Lesson 01: Practical on zphisher
Lesson 02: Practical on Social Engineering Toolkit (SET)
Lesson 01: DoS/DDoS Concepts
Lesson 02: DoS/DDoS Attack Techniques
Lesson 03: DoS/DDoS Tools
Lesson 04: DoS/DDoS Protection Tools and Techniques
Lesson 01: Session Hijacking Concepts
Lesson 02: Session Hijacking Techniques
Lesson 03: Session Hijacking Tools
Lesson 01: SQL Injection Concept
Lesson 02: Types of SQL Injection
Lesson 03: Working Of SQL Injection
Lesson 04: SQL Injection Methodology
Lesson 01: Practical on sqlmap
Lesson 02: Practical on Ghauri
Lesson 01: Fundamentals of Web Application Security
Lesson 02: Common Vulnerabilities in Web Applications
Lesson 03: Best Practices for Web App Security
Lesson 01: Web Server Hacking Techniques
Lesson 02: Server Rooting Methods
Lesson 03: Securing Web servers
Lesson 01: Wireless Network Basics
Lesson 02: Manual Hacking Techniques for Wi-Fi Networks
Lesson 03: Command Line Tools for Wireless Hacking
Lesson 01: Automated Wireless Hacking Tools
Lesson 02: Wireless Network Exploitation Methods
Lesson 03: Wireless Security Best Practices
Lesson 01: Intrusion Detection System (IDS) Evasion Techniques
Lesson 02: Firewall Evasion Methods
Lesson 03: Stealth and Evasion Tools
Lesson 01: Introduction on Honeypots
Lesson 02: Types Of Honeypots
Lesson 03: Install Of Honeypot (KF Sensor)
Lesson 01: Introduction to Buffer Overflow
Lesson 01: What is cryptography, encryption, decryption
Lesson 02: Types of cipher – substitution (Caesar) and Transposition (rail fence) techniques
Lesson 03: Keys in cryptography – asymmetric and symmetric
Lesson 04: What is encoding
Lesson 05: Example of encoding
Lesson 06: What is hashing
Lesson 07: Example of hashes of a string
Lesson 01: Penetration Testing Overview
Lesson 02: Phases of Penetration Testing
Lesson 03: Reporting and Remediation
Lesson 01: Mobile Security Threats
Lesson 02: Exploiting Mobile Platforms
Lesson 03: Theory of mobile and mobile attacks
Lesson 04: Practical of Androrat
Lesson 01: IoT Concepts
Lesson 02: IoT Hacking Methodology
Lesson 03: IoT Hacking Tools
Lesson 04: IoT Security Tools
Lesson 01: Cloud Computing Concepts
Lesson 02: Cloud Computing Threats
Lesson 03: Cloud Computing Attacks
Lesson 04: Cloud Security Tools
Talk to Our Course Advisor
Ethical Hacking Course After 10th
Most importantly, the Ethical Hacking Course with AI Eligibility in most institutions requires an undergraduate degree with a related discipline of Cyber Security, Computer Science, Information Security, and other matching streamlines. However, the institutes of Craw Security at Saket and Laxmi Nagar locations in Delhi NCR can genuinely offer its value-added Ethical Hacking Course After 10th standard from any recognized board in the world.
Apart from that, one can also consider the eligibility to study an Ethical Hacking Course After 12th if one has an original 12th passed certificate from a recognized board anywhere in the world.
Ethical Hacking Corporate Training in Delhi, India
Craw Security provides an abundance of opportunities for corporate professionals to improve their cybersecurity skills by participating in ethical hacking training. These Ethical Hacking with AI Corporate Training in Delhi are intended to provide individuals with the necessary knowledge and skills to identify, evaluate, and mitigate vulnerabilities in corporate networks.
In addition to this, learning participants may develop preventative measures to safeguard their organization’s sensitive data and systems from cyber threats by comprehending the mentality of a potential attacker. Ethical hacking training in Delhi is a valuable investment for businesses that are interested in enhancing their cybersecurity posture and preserving a competitive advantage in the current digital landscape.
Instructor-Led Training
- Blended learning delivery model (instructor-led options)
- Teaching style modified according to the student’s issues
- Develops important personality and career-building skills
- Group Discussions
- 24×7 learner assistance and support
- Weekdays / Weekend Classes
Key Features
- Introduction to Basics of Ethical Hacking
- In-depth Network Scanning
- System Hacking Password Cracking & Bypassing
- Mobile Hacking
- Web Session Hijacking
- Viruses and Worms, Trojan and Back Door, SQL Injection Manual Testing
- Hacking Webservers Server Rooting, Hacking Wireless Network, Penetration Testing: Basics
- Internet of Things (IoT) Hacking, Cloud Security, and many more.
Choose Your Preferred Learning Mode

Classroom Training
We offer customized VILT (Virtual Instructor-Led Training) sessions at your convenient hours to provide effortless training.

Online Training Class

Corporate Training
Hire a preferred trainer at your work premises at your chosen time slots and train your employees with full efficiency.
Ethical Hacking Course Description
Firstly, Craw Cyber Security Institute at Saket and Laxmi Nagar locations in Delhi provides some experienced and skilled InfoSec professionals who can provide the knowledge processing for the Ethical Hacking Course with AI. Within the vicinity of the NCT of Delhi, a quantitive approach is to spread some quality education regarding the Ethical Hacking Course with AI to quantify one’s skill set in information security.
Further, the high-end institutes of Craw Security also deliver ethical hacking courses in Hindi and English to let everyone understand this premium course by heart with basic fundamental level training. Hence, applicants who wish to indulge in a superior learning environment in their own mother tongue — Hindi, which is one of the widely spoken languages in India can certainly come to Craw Security to learn in a pretty helpful environment.
In basic terms, the Ethical Hacking Course with AI in Delhi from the verified and accredited institute of Craw Cyber Security can genuinely transform a basic individual into a full-fledged InfoSec expert who can hack into computers and IT infrastructures like a potential hacker and secure them like a security analyst.
You can also do this splendid Ethical Hacking Course with AI Online via both VILT (Virtual Instructor-Led Training) or through some prerecorded video format that can be accessed in a lifetime via the worthwhile course curriculum of the Craw Cyber Security Institute. In addition to that, it would not be wrong to say that this Ethical Hacking Course with AI is one of the best-selling courses that is chosen by hundreds of learners to start a professional journey to becoming one of the most curated cybersecurity experts in the industry.
Craw Security's Students Awarded











Ethical Hacker Jobs
There is a vast scope of Ethical Hacking Jobs in the world whereas India spots no less than anyone else in the world rankings providing most of the crucial Ethical Hacker Salary in India associated with the varied domains of cybersecurity.
Our alumni network is functioning distinguishably at various levels in reputed organizations after undergoing the Best Certified Ethical Hacking Course with AI in Delhi from Craw Cyber Security Institutions at Saket and Lakshmi Nagar locations. This certifies that a person who completes one’s ethical hacking best practices from Craw Security possesses a decent chance to grab a genuine position at diverse levels in multiple organizations.
Some of those desired Ethical Hacking Jobs are mentioned below:
- Penetration Tester,
- Vulnerability Assessor,
- Information Security Analyst,
- Security Analyst,
- Security Consultant,
- Security Engineer/Architect,
- Information Security Manager, and many more.
Related Cyber Security Course
Latest Blogs
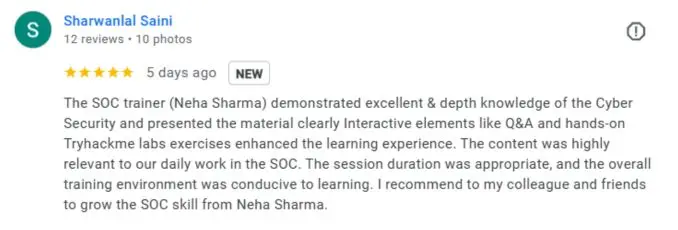
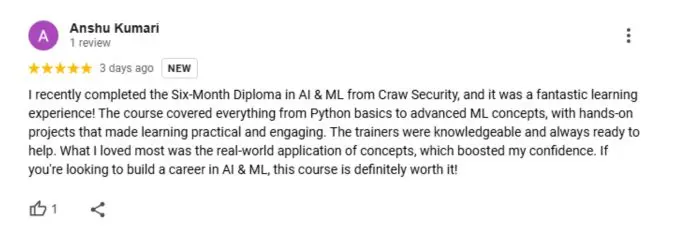
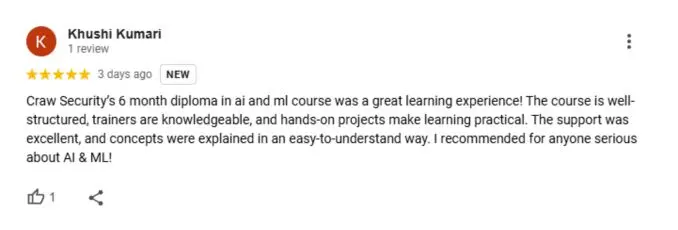
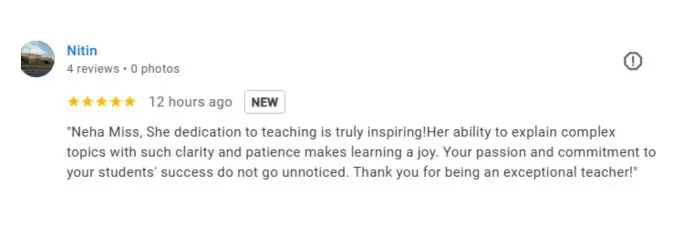
What People Are Saying About Craw Security
Google Review (1900+) ★★★★★
Companies you can get placements in

Students Placed Recently by Craw

Frequently Asked Questions
About the Best Ethical Hacking Institute in India | Ethical Hacking Course in Delhi
Anyone with a deep interest in the domain of Cyber Security and Ethical Hacking Courses with AI in Delhi can certainly join this magnificent Certified Ethical Hacker Training through our dedicated Institute of Craw Cyber Security in Saket and Laxmi Nagar locations in Delhi, India.
Among the numerous courses duly available in the market that deliver crucial information in the genre of Information Security or Ethical Hacking Courses with AI in Delhi, one can sincerely choose Craw Cyber Security Institution to do its world-class Ethical Hacking Course Training through some of the most experienced faculty members and mentors group in the world.
The maximum salary for an ECcouncil Certified Ethical Hacker in India is ₹3,62,366/- per month while the lowest tends to be around ₹17,235/- per month. The average salary of an Ethical Hacker in India turns out to be between ₹29k and ₹41k per month.
The ones who are thinking of switching into this splendid career trajectory of becoming a successful white-hat hacker in the market should reconsider their thought process if they slightly think that it is an easy course to do at any level.
The full-fledged ethical hacker has a lot of responsibilities on one’s shoulders which include some basic processing with the help of good coding skills, genuine penetration testing expertise, and other distinguished parameters. In simple words, ethical hacking is not an easy course to do.
This thing varies from institute to institute as some institutes provide unnecessary extra content to make their course content look lengthy and vast so that they can obtain more money from the pockets of the unaware guardians of their students.
Yes, it’s very certain that pursuing the Certified Ethical Hacking Course with AI in Delhi is a good and shinier career ahead if you have a keen interest in Ethical Hacking and a Cyber Security background. One can nicely join our Certified Ethical Hacking Training and Certifications from Craw Cyber Security Institute in Saket and Laxmi Nagar locations and learn from scratch to become a genuine Cyber Security professional in the shortest possible time.
The main function of an ECcouncil Certified Ethical Hacker is to find the loopholes in the form of threats and vulnerabilities in the servers of a particular website, network, or the IT infrastructure of an organization and secure them by finding the perfect strategy in the shortest time possible.
There are many programming languages in the world widely used by numerous types of potential hackers like Python, Java, C, C++, etc. But most of the hackers use Python as their main coding language partner to do their various hacking stuff in the world. So researchers of the domain also say that Python Programming Language has also been immensely used by many Black Hat Hackers around the world.
Most of the famous Cyber Security and Ethical Hacking Courses with AI in Delhi NCR want a Bachelor’s degree (BSc, BTech, BE, BCA) in Information Technology or Computer Science to become an ethical hacker, whereas Craw Cyber Security is one of the few institutes that provides its genuine curriculum of Ethical Hacking Course with AI in Delhi with a minimum 10th passed certificate Information Technology or Computer Science to become an ethical hacker, whereas Craw Cyber Security is one of the few institutes that provides its genuine curriculum of Ethical Hacking Course with AI in Delhi with a minimum 10th passed certificate from any recognized board in India.
- Computer Networking Skills.
- Computer Skills
- Linux Skills
- Basic Hardware knowledge
- Cryptography Skills
- Database Skills
Ethical hacking, often referred to as penetration testing or white-hat hacking, encompasses the utilization of comparable tools, tactics, and procedures employed by hackers. However, a fundamental distinction lies in the fact that ethical hackers operate with explicit authorization to breach the systems they assess. The primary objective of conducting vulnerability assessments is to identify potential weaknesses in systems, adopting a perspective like that of a malevolent hacker, with the ultimate aim of enhancing system security.
authorization to breach the systems they assess. The primary objective of conducting vulnerability assessments is to identify potential weaknesses in systems, adopting a perspective like that of a malevolent hacker, with the ultimate aim of enhancing system security.
Yes, a person who wishes to join this primetime Ethical Hacking Course with AI in Delhi by Craw Security would need to fulfill the following factors:
- Networking knowledge,
- Python and other programming languages,
- Good knowledge of operating systems like Linux, Ubuntu, Kali Linux, Windows, etc.
At Craw Security, the Ethical Hacking Course with AI in Delhi lasts 60 hours.
Yes, you will certainly grab a valid certificate from FutureSkills Prime, a MeitY – NASSCOM, Digital Skilling Initiative, after completing the successful attempt of the corresponding exam with this course.
- Module 01: Introduction to Basics of Ethical Hacking
- Module 02: Introduction of AI in the world of Ethical Hacking (ShellGPT, TerminalGPT, ChatGPT)
- Module 03: Prompt Engineering for hacking Scripts and payloads.
- Module 04: Foot-printing (Active) Using ShellGPT scripts.
- Module 05: Foot-printing (Passive) Using ShellGPT scripts.
- Module 06: In-depth Network scanning and Advanced AI-Driven Nmap Script Generation
- Module 07: Enumeration User Identification
- Module 08: System Hacking Password Cracking & Bypassing
- Module 09: Developing Viruses and Worms using AI
- Module 10: Developing Trojan and Back Door
- Module 11: Developing Bots and Botnets
- Module 12: Sniffers MITM with Kali
- Module 13: Sniffers MITM with Windows
- Module 14: Social Engineering Techniques Theoretical Approach
- Module 15: Social Engineering Toolkit Practical Based Approach using AI
- Module 16: Denial of Service DOS & DDOS Attacks
- Module 17: Web Session Hijacking
- Module 18: SQL Injection Manual Testing using AI scripts
- Module 19: SQL Injection Automated Tool-Based Testing
- Module 20: Basics of Web App Security
- Module 21: Hacking Web servers using TerminalGPT
- Module 22: Hacking Wireless Networks Manual CLI-Based
- Module 23: Hacking Wireless Network
- Module 24: Evading IDS, Firewall using AI
- Module 25: Honey pots
- Module 26: Buffer Overflow
- Module 27: Cryptography using AI tool.
- Module 28: Penetration Testing: Basics
- Module 29: Mobile Hacking payloads using AI.
- Module 30: Internet of Things (IoT) Hacking
- Module 31: Cloud Security and many more
The cost of the course is highly low for our learners that belong to economically weaker sections. Hence, the cost of this Ethical Hacking Course with AI in Delhi by Craw Security can be checked by making a simple call at +91-9513805401 and having a word with our team of expert educational consultants.
In general, ethical hacking can be termed as the practice of safeguarding diverse IoT devices from harmful attacks initiated by a malicious hacking practitioner. Hence, both are contrary to each other in terms of their working methodologies and intentions.
If you are confused about which programming language should be used in ethical hacking for performing hacking tasks, then the following are some of the most popular computing languages used in ethical hacking:
- Python,
- JavaScript,
- SQL,
- Bash/ Shell Scripting,
- Ruby,
- C/ C++,
- Java,
- PHP,
- Assembly Language, and many more.
To set up a secure and legitimate working environment for hacking, you need to follow the following steps:
- Permission & Authorization,
- Utilize Virtual Machines (VMs),
- Legal Compliance,
- Ethical Guidelines,
- Secure Testing Tools,
- Network Segmentation,
- Data Protection,
- Documentation & Reporting, and
- Continuous Learning and Improvement.
If you want to be an ethical hacker, you must get familiar with various software and tools usually gets used for pentesting, vulnerability testing, and security research. However, some of the popular tools are as follows:
- Nmap,
- Metasploit Framework,
- Burp Suite,
- Wireshark,
- John the Ripper,
- Hydra,
- Aircrack-ng,
- Hashcat,
- OWASP ZAP,
- SQLMap,
- Nessus, and
- Netcat (nc).
An official examination of security measures is called penetration testing; on the other hand, ethical hacking is a more general activity that involves finding and taking advantage of flaws that fall within moral bounds.
Think about the following five points to stay up to date on the newest security flaws and exploits:
- Follow Security News Sources,
- Join Mailing Lists and Forums,
- Monitor Vendor Security Advisories,
- Participate in Security Communities, and
- Attend Security Conferences and Webinars.
When performing a penetration test, ethical concerns are crucial to make sure the testing is carried out properly and within the bounds of the law and ethics. The main ethical factors are as follows:
- Obtain Authorization,
- Define Scope,
- Respect Privacy,
- Minimize Disruption,
- Document Findings,
- Obtain Informed Consent,
- Do No Harm,
- Follow Legal Requirements,
- Maintain Integrity, and
- Continuous Improvement.
The laws, rules, and rules of law that control cybersecurity and computer-related activities establish the bounds of ethical hacking. The following are some important legal restrictions that ethical hackers need to follow:
- Authorization,
- Scope Limitations,
- Data Protection,
- Non-Destructive Testing,
- Legal Compliance,
- Disclosure of Findings,
- Professionalism and Integrity, and
- Documentation and Reporting.
In their interactions with the general public and the companies they represent, ethical hackers have various obligations:
- Protect Public Safety,
- Maintain Confidentiality,
- Act in Good Faith,
- Follow Legal and Ethical Standards,
- Provide Transparent Reporting,
- Educate and Raise Awareness,
- Continuously Improve Skills, and
- Respect Stakeholder Interests.
By abiding by ethical rules, acting truthfully and openly in all of their interactions, and upholding professional norms, ethical hackers can preserve integrity in their work.
Some of the most recognized certifications include:
- Certified Ethical Hacker (CEH),
- CompTIA Security+,
- Offensive Security Certified Professional (OSCP),
- Certified Information Systems Security Professional (CISSP),
- GIAC Certified Penetration Tester (GPEN),
- Certified Penetration Testing Consultant (CPTC),
- Certified Secure Computer User (CSCU), and
- Certified Professional Ethical Hacker (CPEH).
A successful career in ethical hacking requires not only technical expertise but also strong problem-solving, critical thinking, and good communication abilities.
The following are some of the subjects that are often covered in a training course that focuses on ethical hacking and cyber security:
- Fundamentals of Cyber Security,
- Network Security,
- Web Application Security,
- Cryptography,
- Digital Forensics,
- Ethical Hacking,
- Incident Response,
- Compliance and Governance, etc.
Despite the fact that technological expertise is necessary, ethical hackers also require strong commercial skills, such as the following:
- Communication,
- Problem-solving,
- Critical thinking,
- Negotiation,
- Project management, etc.
Technical abilities are essential for professionals working in cyber security, including the following:
- Programming languages,
- Operating systems,
- Networking protocols,
- Database management,
- Security tools, etc.
Ethical hackers can earn varying salaries depending on a variety of factors, including their level of expertise, certifications, location, and the size of their firm. On the other hand, because of the extremely high demand for their expertise, they typically command incomes that are competitive.
You should expect to learn a wide range of tools, including the following:
- Operating systems: Kali Linux, Ubuntu, Windows Server,
- Network scanning tools: Nmap, Nessus,
- Vulnerability scanners: Metasploit, Acunetix,
- Packet analyzers: Wireshark,
- Forensics tools: Autopsy, FTK,
- Programming languages: Python, C++,
- Scripting languages: Bash, PowerShell, etc.
Learning Cyber Security and Ethical Hacking can be accomplished in a number of different ways:
- Online courses,
- Bootcamps,
- Degree programs,
- Certifications, etc.
Yes, many institutes even provide a genuine option to all the learners to choose from a variety of their partner organizations for doing a proper internship. For example, you may join Craw Cyber Security Institute for an internship program in cyber security and ethical hacking courses.
Job opportunities in the fields of ethical hacking and cyber security are extensive and continue to expand. The following are some examples of common roles in the fields of Cyber Security & Ethical Hacking:
- Security analyst,
- Penetration tester,
- Security engineer,
- Incident responder,
- Digital forensics investigator,
- Security architect,
- Information security manager, etc.
Craw Security has a dedicated team of educational counselors who can provide highly authentic and genuine cybersecurity career mentoring sessions duly organized and effective. To contact the team of educational counselors at Craw Security, you can give us a call at our 24X7 hotline number +91-9513805401.
The goals of an ethical hacking course are to deliver learners with an organized learning experience, practical experience, and a strong basis in the fundamentals of cybersecurity. These classes are not only for beginners; those with years of experience in the field of information technology can gain something by staying current with the most recent technologies and trends.
You should think about enrolling in an ethical hacking course for the following reasons:
- High Demand for Ethical Hackers: As the number of cyber risks continues to climb, businesses are becoming more desperate for professionals who are skilled in ethical hacking activities.
- Lucrative Career Opportunities: The salaries of ethical hackers are rather high, and certifications such as CEH (Certified Ethical Hacker) add a great amount of value to your resume.
- Comprehensive Skill Development: A comprehensive education in cybersecurity is provided by these classes, which cover a wide range of topics on cybersecurity, from network security to penetration testing.









