The Top 10 Web Attacks That Defined Cybersecurity Battles

The Top 10 Web Attacks That Defined Cybersecurity Battles
Top 10 Web Attacks
Introduction:
The prevalence and complexity of web attacks have seen a notable escalation throughout the course of time. As the level of global digital interconnectivity increases, the magnitude and range of these potential risks expand. We need to understand that safeguarding against these below-mentioned web attacks necessitates the implementation of robust security measures, ongoing surveillance, periodic updates and patches, and the dissemination of knowledge to users regarding potential vulnerabilities.
In the dynamic universe of web security, it is crucial to remain well-informed and proactive in order to effectively navigate the ongoing refinement of attack strategies by malicious actors.
This article is an overview of the ten most prominent web attacks that are closely monitored by cybersecurity experts.
1. SQL Injection (SQLi)
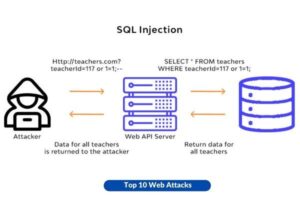
The phenomenon under consideration takes place when an assailant strategically injects malevolent SQL code into a query. If databases are not adequately secured, they can be susceptible to unauthorized access, manipulation, or deletion by this particular approach.
2. Cross-Site Scripting (XSS)
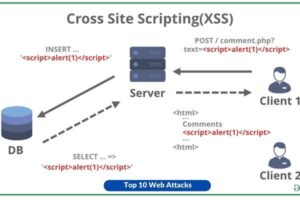
Malicious scripts are injected by attackers into websites, afterward being executed by browsers of unwary users. These vulnerabilities have the potential to result in unauthorized access to sensitive data, the interception of user sessions, or the manipulation of web traffic for malicious purposes.
3. Cross-Site Request Forgery (CSRF)
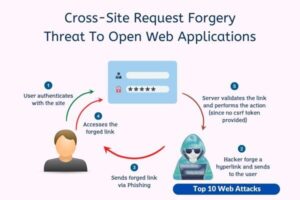
The perpetrator employs deceptive tactics to manipulate the unsuspecting individual into engaging in activities on a website while being verified, unbeknownst to them. This has the potential to result in undesired alterations or actions being carried out on the data.
4. Man-in-the-Middle (MitM) Attacks
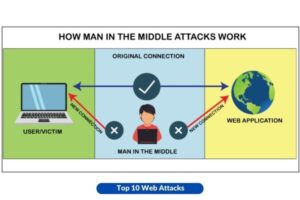
The communication between two parties is intercepted by attackers. This action can be undertaken with the intention of covertly listening to or assuming the identity of one of the participants, so creating the illusion of a typical interaction.
5. DDoS Attacks
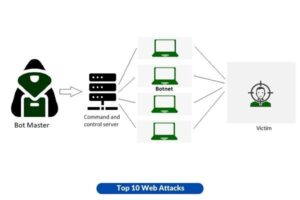
The website is subjected to a distributed denial-of-service (DDoS) attack, wherein a botnet is typically employed to inundate the site with a high volume of traffic. The inundation of servers results in the malfunctioning of websites, rendering them inaccessible to legitimate users.
6. Drive-By Downloads
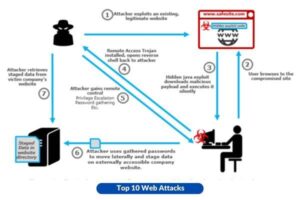
Unwary individuals access a website, unaware that their devices are being subjected to the covert download and installation of malware, which may subsequently facilitate a range of criminal actions.
7. Phishing

Cybercriminals engage in the creation of counterfeit iterations of authentic websites with the intention of deceiving users into divulging sensitive information, such as login credentials, credit card numbers, or personal details.
8. File Inclusion Vulnerabilities
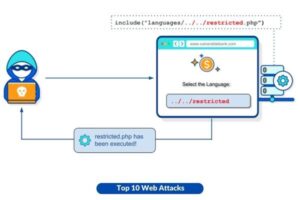
The exploitation of scripts executed on the server, when the input validation process is inadequately performed, is a common strategy employed by attackers. The presence of Remote File Inclusion (RFI) or Local File Inclusion (LFI) can result in the execution of malicious programs by the attacker.
9. Security Misconfiguration
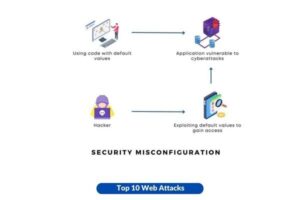
This pertains to the exploitation of default configurations, insufficient setups, or verbose error messages by attackers, resulting in the unlawful acquisition of sensitive data or access to functionalities.
10. Unvalidated Redirects and Forwards
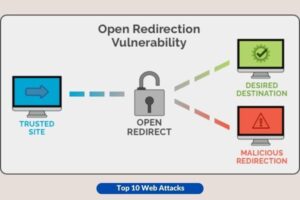
Web applications frequently employ the practice of redirecting users to alternative pages or external websites. If these redirects are not checked, it is possible for attackers to reroute victims to websites that engage in phishing activities or distribute malware.
Enhance Your Knowledge of Preventing Web Attacks with Craw Security
You may also enhance your knowledge base regarding the Top 10 Web Attacks present in the current market conditions, which give troublesome conditions to penetration testers as well as varied organizations. In addition, you may keep them aside by gathering useful information related to them and the genuine best practices to avert them safely.
To do this, you can nicely join Craw Security’s world-class Web Application Security Course in the Saket and Laxmi Nagar institutes in Delhi NCR, where you will find highly skilled and talented training professionals with many years of quality experience in their respective fields. To get more information in the same context, call +91-9513805401 now.

















