Top 10 Hacking Attacks | Craw Security

Top 10 Hacking Attacks | Craw Security
Top 10 Hacking Attacks
Introduction:
Over the course of the digital era, hacking attacks have undergone a progression in both magnitude and complexity. The act of hacking has evolved into a significant concern for security professionals on a global scale, ranging from targeted attacks on individuals to organized campaigns against entire governments. This analysis aims to explore the ten most significant hacking attacks that had a profound impact on the digital domain.
Moreover, you will grab all the genuine details that are some of the most evolved hacking attacks nowadays. In addition to this, these top 10 hacking attacks are giving the most trouble to penetration testers in today’s world.
1. Stuxnet (2010)
The Iranian nuclear facilities were the specific targets of a malevolent worm. Stuxnet, widely attributed to the collaboration between U.S. and Israeli intelligence agencies, inflicted significant harm on Iran’s nuclear program by inducing uncontrolled spinning of its centrifuges.
2. Heartbleed (2014)
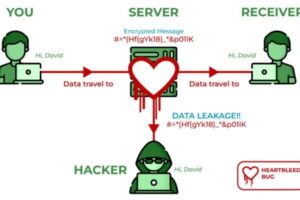
The Heartbleed vulnerability in the OpenSSL cryptographic library resulted in the unauthorized exposure of user data on about two-thirds of the internet, encompassing sensitive information such as passwords, credit card numbers, and confidential documents.
3. Sony Pictures Hack (2014)
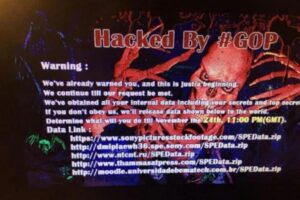
It has been purported that hackers from North Korea purportedly directed their efforts at Sony Pictures purportedly as a form of retribution for the release of the film “The Interview”. The unauthorized disclosure encompassed a range of materials, including unreleased films, confidential correspondence, and personal information of employees.
4. WannaCry Ransomware Attack (2017)
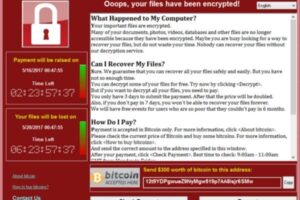
The WannaCry ransomware, which is suspected to have been created by the U.S. National Security Agency (NSA), was employed by hackers to target and compromise over 200,000 machines in 150 nations. This malicious software had severe consequences, causing significant disruptions to hospitals, businesses, and residential users.
5. Equifax Breach (2017)

The breach of financial data in question is a significant event in terms of scale, as hackers managed to infiltrate the personal information of a substantial number of Equifax customers, totaling 147 million individuals. This compromised data included sensitive details such as Social Security numbers and driver’s license numbers.
6. NotPetya Attack (2017)

The ransomware initially focused on Ukrainian enterprises by utilizing a tax program as its means of infiltration. However, it subsequently spread on a global scale, impacting prominent organizations such as Maersk and Merck, resulting in significant financial losses amounting to billions of dollars.
7. Operation Aurora (2009)

This series of cyber-espionage assaults, which had its origins in China, specifically targeted prominent multinational organizations, with Google being among the affected entities. The hackers sought to acquire unauthorized access to IP addresses and personal accounts belonging to individuals involved in the promotion and protection of human rights.
8. Yahoo Data Breach (2013-2014)

The breach, which came to light in 2016, impacted the entirety of Yahoo’s user base, comprising a staggering 3 billion individuals. The compromised data consisted of personal information such as names, email addresses, phone numbers, and hashed passwords.
9. Target Stores Data Breach (2013)

Target experienced a security breach wherein unauthorized individuals gained access to their computer systems, resulting in the compromise of credit and debit card data belonging to 40 million customers, as well as the personal information of an additional 70 million individuals.
10. EternalBlue Exploit (2017)
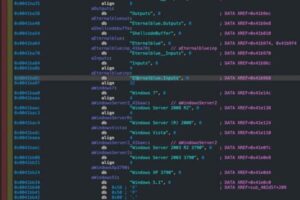
The Windows exploit in question was initially developed as a tool by the National Security Agency (NSA), but it was subsequently disclosed to the public by a collective known as the Shadow Brokers. It served as the foundation for other cyber-attacks, such as WannaCry and NotPetya.
Give The Gift of Knowledge of Ethical Hacking Fundamentals To Yourself
It is always better to understand things personally than go on the topics briefly. Hence, we advise you to take a comprehensive Ethical Hacking Course by Craw Security, the Best Cybersecurity Training Institute in India, with a full-on track record of shaping the lives of future-borne cybersecurity enthusiasts. Call now at +91-9513805401 and have all your doubts cleared with our highly professional team of professional educational consultants.
Read More Blogs
1. Top 10 Hackers in Delhi NCR
2. Top 10 Cyber Lawyers in India
3. Top 30 Ethical Hacking Tools
















